Installation de rkhunter
[root@coffee chris]# yum --enablerepo=epel -y install rkhunter [root@coffee chris]# rkhunter --versioncheck

Configurer rkhunter
[root@coffee chris]# vi /etc/sysconfig/rkhunter
# System configuration file for Rootkit Hunter which # stores RPM system specifics for cron run, etc. # # MAILTO= <email address to send scan report> # DIAG_SCAN= no - perform normal report scan # yes - perform detailed report scan # (includes application check) MAILTO=chris@en-images.info DIAG_SCAN=yes
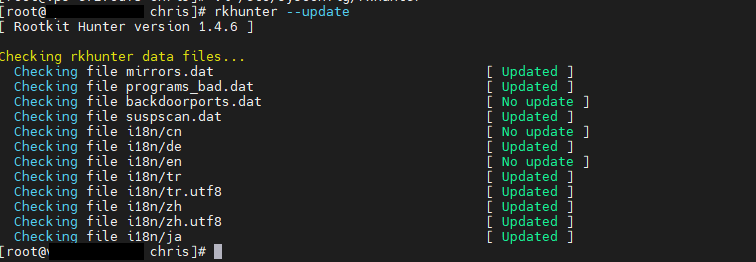
Update base rkhunter et porperties
[root@coffee chris]# rkhunter --update
[root@coffee chris]# rkhunter --propupd

Check Rootkit
[root@coffee chris]# rkhunter --check --sk
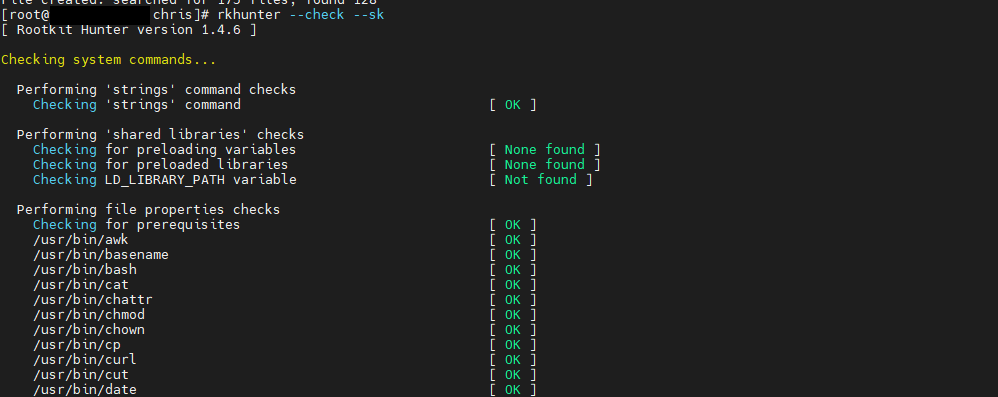
Il va check tous les binaires

Check des rootkit présent sur la machine
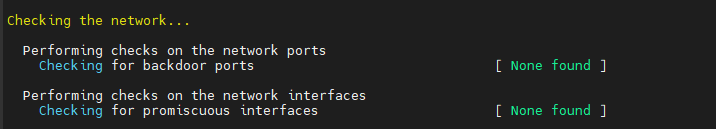
Check la partie réseau
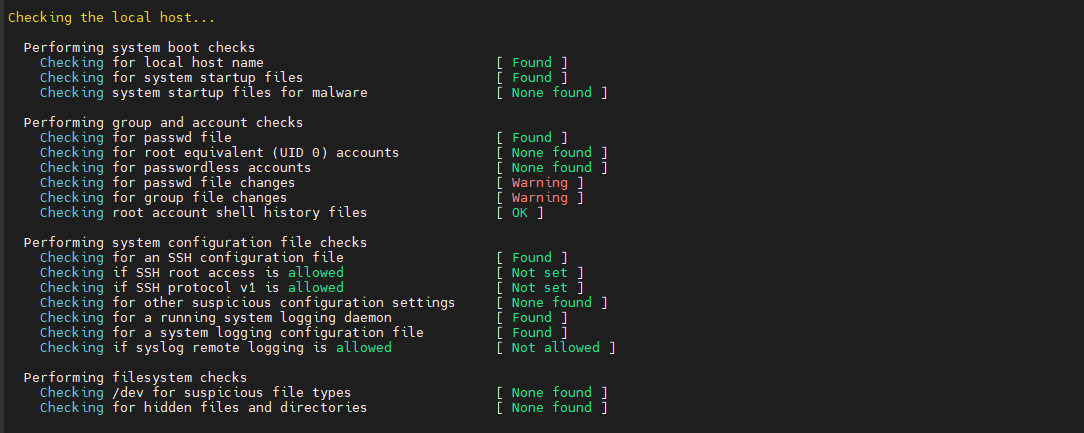
Check le local hosts

Résumé des scans de fichier via rkhunter
Automatiser le scan
[root@coffee chris]# vi /home/rkhunter.sh
#!/bin/sh ( /usr/bin/rkhunter --versioncheck /usr/bin/rkhunter --update /usr/bin/rkhunter --cronjob --report-warnings-only ) | /bin/mail -s 'rkhunter Daily Scan Report (coffeebreak)' chris@en-images.info
[root@coffee chris]# chmod +x /home/rkhunter.sh
[root@coffee chris]# vi /etc/rkhunter.conf MAIL-ON-WARNING= "chris@en-images.info" MAIL_CMD=mail -s "[rkhunter] Warnings found for ${HOST_NAME}" ALLOW_SSH_ROOT_USER=yes
Autoriser root Login SSH
[root@coffee chris]# vi /etc/ssh/sshd_config PermitRootLogin yes [root@coffee chris]# systemctl reload sshd
Crontab tous les jours à 12H00
[root@coffee chris]# systemctl start crond.service [root@coffee chris]# systemctl enable crond.service
[root@coffee chris]# crontab -e # Tous les jours à 12H00 00 12 * * * /usr/bin/sh /home/rkhunter.sh
[root@coffee chris]# tail -f /var/log/rkhunter/rkhunter.log
Dans les logs

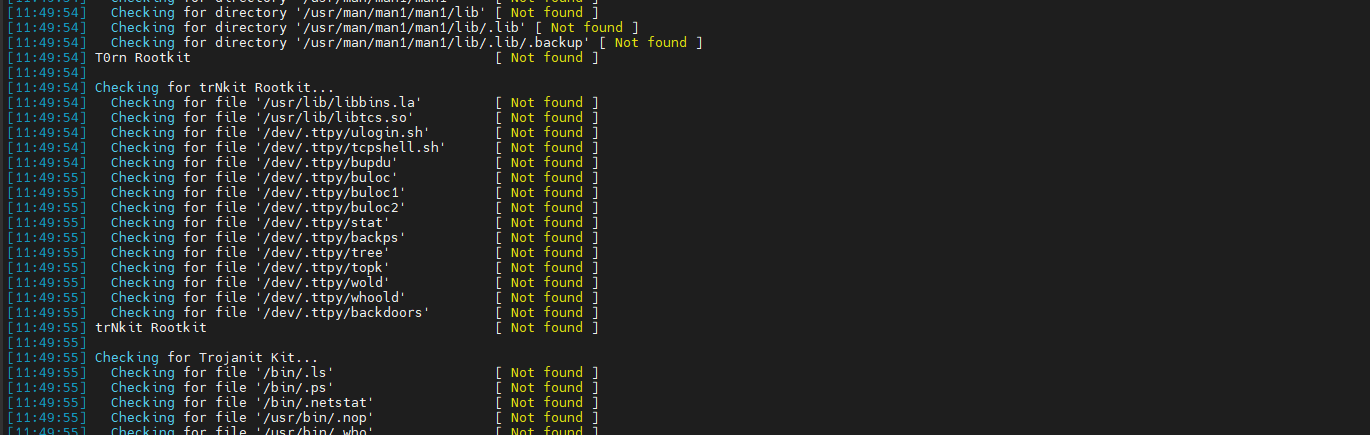
Check des rootKIT
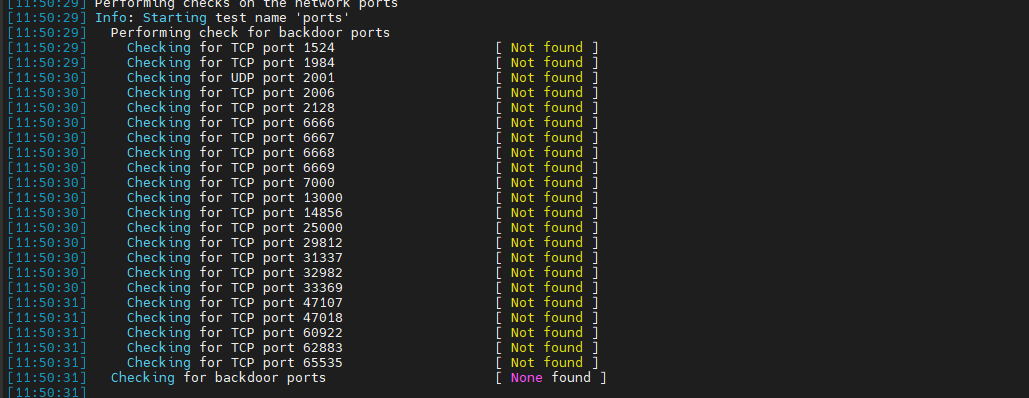
Check TCP port RootKit

Mail Rapport de rootKIT

Message Mail « Infection »

Views: 11