Installation de la machine tun-hosta.house.cpb – RockyLinux
Spécification de la machine tun-hosta.house.cpb
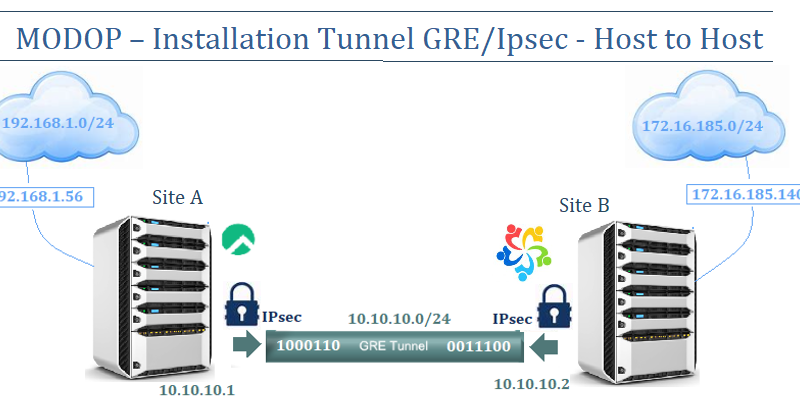
Host : tun-hosta.house.cpb
- IP :192.168.1.56
- VIP : 10.10.10.1/24
- OS : RockyLinux
- vCPU : 2
- DD : 8Go
- Ram : 2Go
Mise à jour de la machine
[root@tun-hosta ~]# dnf update -y
TimeDate
[root@tun-hosta ~]# timedatectl set-timezone "Europe/Paris"
Ajouter les hosts (Si pas de DNS)
[root@tun-hosta ~]# echo "192.168.1.56 tun-hosta tun-hosta.house.cpb" >> /etc/hosts [root@tun-hosta ~]# echo "172.16.185.140 tun-hostb tun-hostb.house.cpb" >> /etc/hosts [root@tun-hosta ~]# echo "10.10.10.1 tunipsec-grea tunipsec-grea.house.cpb" >> /etc/hosts [root@tun-hosta ~]# echo "10.10.10.2 tunipsec-greb tunipsec-greb.house.cpb" >> /etc/hosts
Installation epel
[root@tun-hosta ~]# dnf install epel-release
Chargement Module GRE – CLI
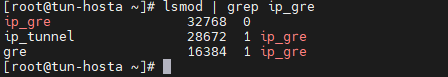
[root@tun-hosta ~]# lsmod | grep ip_gre [root@tun-hosta ~]# modprobe ip_gre [root@tun-hosta ~]# lsmod | grep ip_gre
Chargement Module GRE – On BOOT
[root@tun-hosta ~]# echo ip_gre >> /etc/modules-load.d/tun.conf [root@tun-hosta ~]# ls -al /etc/modules-load.d/tun.conf -rw-r--r--. 1 root root 7 19 juin 12:13 /etc/modules-load.d/tun.conf
Configuration Réseau Tunnel GRE
Création du Tunnel tun0
[root@tun-hosta ~]# ip tunnel add tun0 mode gre remote 172.16.185.140 local 192.168.1.56 ttl 255
Activation de la connexion tun0
[root@tun-hosta ~]# ip link set tun0 up
Création de l’adresse VIP
[root@tun-hosta ~]# ip addr add 10.10.10.1/24 dev tun0
Chargement Tun0 – On BOOT
[root@tun-hosta ~]# echo "ip tunnel add tun0 mode gre remote 172.16.185.140 local 192.168.1.56 ttl 255" >> /etc/rc.local [root@tun-hosta ~]# echo "ip link set tun0 up" >> /etc/rc.local [root@tun-hosta ~]# echo "ip addr add 10.10.10.1/24 dev tun0" >> /etc/rc.local [root@tun-hosta ~]# chmod +x /etc/rc.local
Check de la connexion tun0
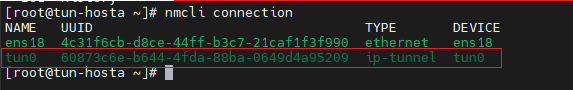
[root@tun-hosta ~]# nmcli connection
[root@tun-hosta ~]# ip a show tun0

Activer le Forward IPv4
[root@tun-hosta ~]# echo "net.ipv4.ip_forward=1" > /etc/sysctl.conf [root@tun-hosta ~]# echo "net.ipv4.conf.default.send_redirects=0 " > /etc/sysctl.conf [root@tun-hosta ~]# echo "net.ipv4.conf.default.accept_redirects=0 " > /etc/sysctl.conf [root@tun-hosta ~]# sysctl -p
Activer/désactiver les rules Firewall GRE
[root@tun-hosta ~]# firewall-cmd --remove-service={dhcpv6-client,cockpit} –permanent [root@tun-hosta ~]# firewall-cmd --permanent --add-interface=tun0 [root@tun-hosta ~]# firewall-cmd --permanent --direct --add-rule ipv4 filter INPUT 0 -p gre -j ACCEPT [root@tun-hosta ~]# firewall-cmd --reload
Installation de la machine tun-hostb.house.cpb – AlmaLinux8
Spécification de la machine tun-hostb.house.cpb
Host : tun-hostb.house.cpb
- IP :172.16.185.140
- VIP : 10.10.10.2/24
- OS : AlmaLinux
- vCPU : 2
- DD : 8Go
- Ram : 2Go
Mise à jour de la machine
[root@tun-hostb ~]# yum -y update
TimeDate
[root@tun-hostb ~]# timedatectl set-timezone "Europe/Paris"
Ajouter les hosts (Si pas de DNS)
[root@tun-hostb ~]# echo "192.168.1.56 tun-hosta tun-hosta.house.cpb" >> /etc/hosts [root@tun-hostb ~]# echo "172.16.185.140 tun-hostb tun-hostb.house.cpb" >> /etc/hosts [root@tun-hostb ~]# echo "10.10.10.1 tunipsec-grea tunipsec-grea.house.cpb" >> /etc/hosts [root@tun-hostb ~]# echo "10.10.10.2 tunipsec-greb tunipsec-greb.house.cpb" >> /etc/hosts
Chargement Module GRE – CLI
[root@tun-hostb ~]# lsmod | grep ip_gre [root@tun-hostb ~]# modprobe ip_gre
Chargement Module GRE – On BOOT
[root@tun-hostb ~]# echo ip_gre >> /etc/modules-load.d/tun.conf
Configuration Réseau Tunnel GRE
Création de l’interface tun0
[root@tun-hostb ~]# ip tunnel add tun0 mode gre remote 192.168.1.56 local 172.16.185.140 ttl 255
Activation de la connexion tun0
[root@tun-hostb ~]# ip link set tun0
Création de l’adresse VIP
[root@tun-hostb ~]# ip addr add 10.10.10.2/24 dev tun0
Chargement Tun0 – On BOOT
[root@tun-hosta ~]# echo "ip tunnel add tun0 mode gre remote 192.168.1.56 local 172.16.185.140 ttl 255" >> /etc/rc.local [root@tun-hosta ~]# echo "ip link set tun0 up" >> /etc/rc.local [root@tun-hosta ~]# echo "ip addr add 10.10.10.2/24 dev tun0" >> /etc/rc.local [root@tun-hosta ~]# chmod +x /etc/rc.local
Check de la connexion tun0
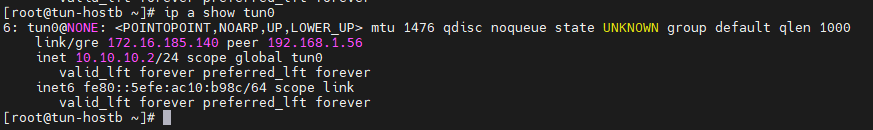
[root@tun-hostb ~]# ip a show tun0
[root@tun-hostb ~]# nmcli connection
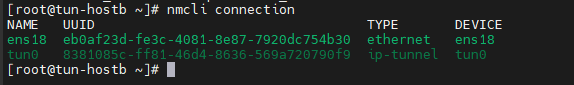
Activer le Forward IPv4
[root@tun-hostb ~]# echo "net.ipv4.ip_forward=1" > /etc/sysctl.conf [root@tun-hostb ~]# echo "net.ipv4.conf.default.send_redirects=0 " > /etc/sysctl.conf [root@tun-hostb ~]# echo "net.ipv4.conf.default.accept_redirects=0 " > /etc/sysctl.conf [root@tun-hostb ~]# sysctl -p
Activer/désactiver les rules Firewall GRE
[root@tun-hostb ~]# firewall-cmd --remove-service=dhcpv6-client –permanent [root@tun-hostb ~]# firewall-cmd --permanent --add-interface=tun0 [root@tun-hostb ~]# firewall-cmd --permanent --direct --add-rule ipv4 filter INPUT 0 -p gre -j ACCEPT [root@tun-hostb ~]# firewall-cmd --reload
Check des flux réseaux Public et Tunnel
Serveur tun-hosta
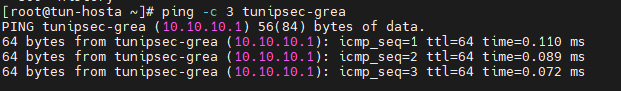
[root@tun-hosta ~]# ping -c 3 tunipsec-grea
[root@tun-hosta ~]# ping -c 3 tunipsec-greb

Serveur tun-hostb
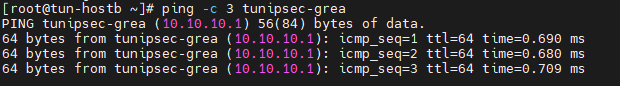
[root@tun-hostb ~]# ping -c 3 tunipsec-grea
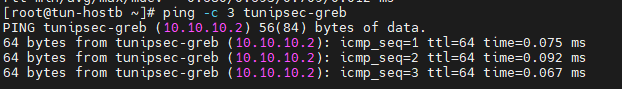
[root@tun-hostb ~]# ping -c 3 tunipsec-greb
Installation Ipsec sur le Tunnel tun0
Inventaire du réseau tun0/Machine
Host : tunipsec-grea.house.cpb
- IP tun0 : 10.10.10.1/24
Host : tunipsec-greb.house.cpb
- IP tun0 : 10.10.10.2/24
Ipsec – Machine tunipsec-grea.house.cpb
Désactiver « rp_filter »
[root@tun-hosta ~]# echo "net.ipv4.conf.all.rp_filter = 0" >> /etc/sysctl.d/50-libreswan.conf [root@tun-hosta ~]# sysctl --system
Installer libreswan
[root@tun-hosta ~]# yum install libreswan
Initialisation de la base NSS
[root@tun-hosta ~]# systemctl stop ipsec [root@tun-hosta ~]# rm -f /etc/ipsec.d/*db [root@tun-hosta ~]# ls -al /etc/ipsec.d/

[root@tun-hosta ~]# ipsec initnss Initializing NSS database [root@tun-hosta ~]# ls -al /etc/ipsec.d/

Ajouter les rules ipsec – firewall
[root@tun-hosta ~]# firewall-cmd --add-service=ipsec --permanent && firewall-cmd –reload
Démarrer Ipsec
[root@tun-hosta ~]# systemctl enable ipsec --now
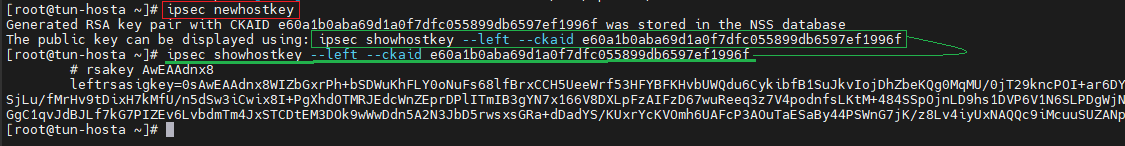
Génerer une clef RSA pour hosta
[root@tun-hosta ~]# ipsec newhostkey Generated RSA key pair with CKAID e60a1b0aba69d1a0f7dfc055899db6597ef1996f was stored in the NSS database The public key can be displayed using: ipsec showhostkey --left --ckaid e60a1b0aba69d1a0f7dfc055899db6597ef1996f [root@tun-hosta ~]# ipsec showhostkey --left --ckaid e60a1b0aba69d1a0f7dfc055899db6597ef1996f # rsakey AwEAAdnx8 leftrsasigkey=0sAwEAAdnx8WIZbGxrPh+bSDWuKhFLY0oNuFs68lfBrxCCH5UeeWrf53HFYBFKHvbUWQdu6CykibfB1SuJkvIojDhZbeKQg0MqMU/0jT29kncPOI+ar6DYIu0yXUnlIOYwqJQwFAWAXBPLA4b2JsePKZJFcjtlryRaItfWxdkDH39aO/WlSjLu/fMrHv9tDixH7kMfU/n5dSw3iCwix8I+PgXhdOTMRJEdcWnZEprDPlITmIB3gYN7x166V8DXLpFzAIFzD67wuReeq3z7V4podnfsLKtM+484SSpOjnLD9hs1DVP6V1N6SLPDgWjNXEaDjBXYfllrJzGl62If9+DiRHzA3XQn7XDXAxqzoDKpW4IBMVo6EHzK5Lj/GgC1qvJdBJLf7kG7PIZEv6LvbdmTm4JxSTCDtEM3DOk9wWwDdn5A2N3JbD5rwsxsGRa+dDadYS/KUxrYcKVOmh6UAFcP3AOuTaESaBy44PSWnG7jK/z8Lv4iyUxNAQQc9iMcuuSUZANpPvdX5ze3QXkr/ny7qw==
Ipsec – Machine tunipsec-greb.house.cpb
Désactiver « rp_filter »
[root@tun-hostb ~]# echo "net.ipv4.conf.all.rp_filter = 0" >> /etc/sysctl.d/50-libreswan.conf [root@tun-hostb ~]# sysctl --system
Installer libreswan
[root@tun-hostb ~]# yum install libreswan
Initialisation de la base NSS
[root@tun-hostb ~]# systemctl stop ipsec [root@tun-hostb ~]# rm -f /etc/ipsec.d/*db [root@tun-hostb ~]# ipsec initnss Initializing NSS database [root@tun-hostb ~]# ls -al /etc/ipsec.d/

Ajouter les rules ipsec – firewall
[root@tun-hostb ~]# firewall-cmd --add-service=ipsec --permanent && firewall-cmd --reload
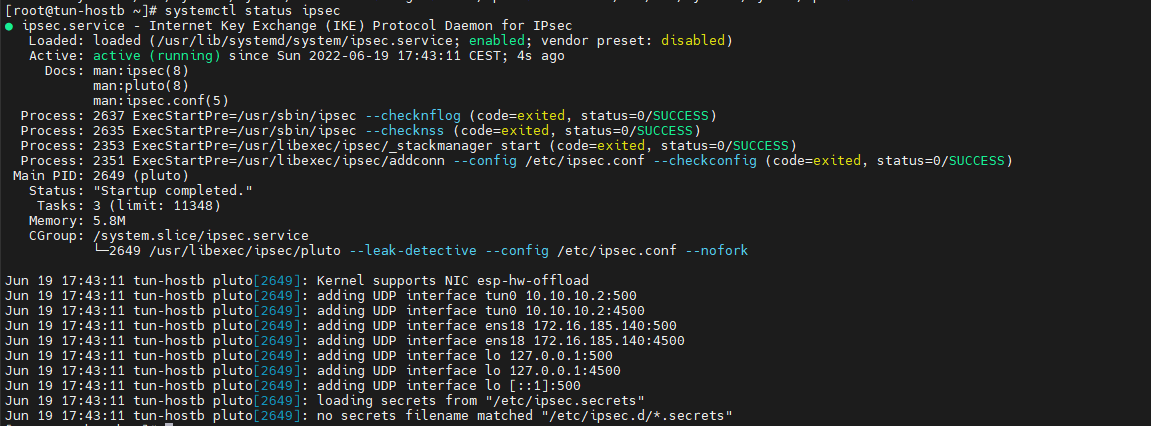
Démarrer Ipsec
[root@tun-hostb ~]# systemctl enable ipsec --now [root@tun-hostb ~]# systemctl status ipsec
Génerer une clef RSA pour hostb
[root@tun-hostb ~]# ipsec newhostkey Generated RSA key pair with CKAID 2f5cd8184f8878367711840329cd53904c8fc117 was stored in the NSS database The public key can be displayed using: ipsec showhostkey --left --ckaid 2f5cd8184f8878367711840329cd53904c8fc117 [root@tun-hostb ~]# ipsec showhostkey --left --ckaid 2f5cd8184f8878367711840329cd53904c8fc117 # rsakey AwEAAengQ leftrsasigkey=0sAwEAAengQzda3EZwsJSqi9zaF3EtlMy09xN4T1u5/i0pmXzJGUe3A0qfOEG4zueQ3Cy7VstC4EwdrrPccYJf82k1jX2yjgIR8enWbprkI2fDWt0++/e/lxw8/6HNEo9V7hWCPMWqo9TWTwu2qM/kZJgylY538SYe+LTG1MmsWDhoF4ZqfedwDL85ZGpsGsBlaJPxH1TNcLn2lLf8sTNJO2I6br8rSQl1OAp1SawAoBgwxgHsCLvpAUhQCtFRTYjf3WayrtMvEgmKZjcrV5xlNR1jYDHOx6RLd6eu1JMR9k8JUwuNeeEbtoKqdNBQBia7jZMi0Cl9NpaWtdcvMFq533hbitS8kHvzDHpOu4wsr9RCwGyyWfSPQbJr5fbCMa942SAOWLLXHdo4/VHXRlogj3Fj23BP/e4giB5ARdxHQxreSxZLUewilgxQlM4GaGsSGCu49ZikoQf0Fm1hEVeIjwgpEa26lLCtQ+mGGWw+y59xlPa+2pZDLQt26fTUIVovCGzqgzzEAo7qOXpQ7A9A7yykcV1yQzkVKmpeUmt2FzLL1r91qnIGy3E1mdt0Rom2xI9gJrneGH/rWq4GtVNfEsv6TImJCRyd9FIjK4qnH+hTyT1uPTM28cfWs3mUmbqtSb8uPRe9WFq0i459Qzwz2BWB5pM=
Création Ipsec Host-to-Host
Inventaire des Hosts de l’infrastructure
Host : tunipsec-grea.house.cpb
- IP tun0 : 10.10.10.1/24
- RSA : 0sAwEAAdnx8WIZbGxrPh+bSDWuKhFLY0oNuFs68lfBrxCCH5UeeWrf53HFYBFKHvbUWQdu6CykibfB1SuJkvIojDhZbeKQg0MqMU/0jT29kncPOI+ar6DYIu0yXUnlIOYwqJQwFAWAXBPLA4b2JsePKZJFcjtlryRaItfWxdkDH39aO/WlSjLu/fMrHv9tDixH7kMfU/n5dSw3iCwix8I+PgXhdOTMRJEdcWnZEprDPlITmIB3gYN7x166V8DXLpFzAIFzD67wuReeq3z7V4podnfsLKtM+484SSpOjnLD9hs1DVP6V1N6SLPDgWjNXEaDjBXYfllrJzGl62If9+DiRHzA3XQn7XDXAxqzoDKpW4IBMVo6EHzK5Lj/GgC1qvJdBJLf7kG7PIZEv6LvbdmTm4JxSTCDtEM3DOk9wWwDdn5A2N3JbD5rwsxsGRa+dDadYS/KUxrYcKVOmh6UAFcP3AOuTaESaBy44PSWnG7jK/z8Lv4iyUxNAQQc9iMcuuSUZANpPvdX5ze3QXkr/ny7qw==
Host : tunipsec-greb.house.cpb
- IP tun0 : 10.10.10.2/24
- RSA : 0sAwEAAengQzda3EZwsJSqi9zaF3EtlMy09xN4T1u5/i0pmXzJGUe3A0qfOEG4zueQ3Cy7VstC4EwdrrPccYJf82k1jX2yjgIR8enWbprkI2fDWt0++/e/lxw8/6HNEo9V7hWCPMWqo9TWTwu2qM/kZJgylY538SYe+LTG1MmsWDhoF4ZqfedwDL85ZGpsGsBlaJPxH1TNcLn2lLf8sTNJO2I6br8rSQl1OAp1SawAoBgwxgHsCLvpAUhQCtFRTYjf3WayrtMvEgmKZjcrV5xlNR1jYDHOx6RLd6eu1JMR9k8JUwuNeeEbtoKqdNBQBia7jZMi0Cl9NpaWtdcvMFq533hbitS8kHvzDHpOu4wsr9RCwGyyWfSPQbJr5fbCMa942SAOWLLXHdo4/VHXRlogj3Fj23BP/e4giB5ARdxHQxreSxZLUewilgxQlM4GaGsSGCu49ZikoQf0Fm1hEVeIjwgpEa26lLCtQ+mGGWw+y59xlPa+2pZDLQt26fTUIVovCGzqgzzEAo7qOXpQ7A9A7yykcV1yQzkVKmpeUmt2FzLL1r91qnIGy3E1mdt0Rom2xI9gJrneGH/rWq4GtVNfEsv6TImJCRyd9FIjK4qnH+hTyT1uPTM28cfWs3mUmbqtSb8uPRe9WFq0i459Qzwz2BWB5pM=
Fichier de conf Ipsec sur hosta
[root@tun-hosta ~]# vi /etc/ipsec.d/host_to_host.conf
conn tunnelVPN leftid=@west left=10.10.10.1 leftrsasigkey=0sAwEAAdnx8WIZbGxrPh+bSDWuKhFLY0oNuFs68lfBrxCCH5UeeWrf53HFYBFKHvbUWQdu6CykibfB1SuJkvIojDhZbeKQg0MqMU/0jT29kncPOI+ar6DYIu0yXUnlIOYwqJQwFAWAXBPLA4b2JsePKZJFcjtlryRaItfWxdkDH39aO/WlSjLu/fMrHv9tDixH7kMfU/n5dSw3iCwix8I+PgXhdOTMRJEdcWnZEprDPlITmIB3gYN7x166V8DXLpFzAIFzD67wuReeq3z7V4podnfsLKtM+484SSpOjnLD9hs1DVP6V1N6SLPDgWjNXEaDjBXYfllrJzGl62If9+DiRHzA3XQn7XDXAxqzoDKpW4IBMVo6EHzK5Lj/GgC1qvJdBJLf7kG7PIZEv6LvbdmTm4JxSTCDtEM3DOk9wWwDdn5A2N3JbD5rwsxsGRa+dDadYS/KUxrYcKVOmh6UAFcP3AOuTaESaBy44PSWnG7jK/z8Lv4iyUxNAQQc9iMcuuSUZANpPvdX5ze3QXkr/ny7qw== rightid=@east right=10.10.10.2 rightrsasigkey=0sAwEAAengQzda3EZwsJSqi9zaF3EtlMy09xN4T1u5/i0pmXzJGUe3A0qfOEG4zueQ3Cy7VstC4EwdrrPccYJf82k1jX2yjgIR8enWbprkI2fDWt0++/e/lxw8/6HNEo9V7hWCPMWqo9TWTwu2qM/kZJgylY538SYe+LTG1MmsWDhoF4ZqfedwDL85ZGpsGsBlaJPxH1TNcLn2lLf8sTNJO2I6br8rSQl1OAp1SawAoBgwxgHsCLvpAUhQCtFRTYjf3WayrtMvEgmKZjcrV5xlNR1jYDHOx6RLd6eu1JMR9k8JUwuNeeEbtoKqdNBQBia7jZMi0Cl9NpaWtdcvMFq533hbitS8kHvzDHpOu4wsr9RCwGyyWfSPQbJr5fbCMa942SAOWLLXHdo4/VHXRlogj3Fj23BP/e4giB5ARdxHQxreSxZLUewilgxQlM4GaGsSGCu49ZikoQf0Fm1hEVeIjwgpEa26lLCtQ+mGGWw+y59xlPa+2pZDLQt26fTUIVovCGzqgzzEAo7qOXpQ7A9A7yykcV1yQzkVKmpeUmt2FzLL1r91qnIGy3E1mdt0Rom2xI9gJrneGH/rWq4GtVNfEsv6TImJCRyd9FIjK4qnH+hTyT1uPTM28cfWs3mUmbqtSb8uPRe9WFq0i459Qzwz2BWB5pM= authby=rsasig auto=start
Mise en place du Tunnel Ipsec hosta – l’encapsulation tun0
[root@tun-hosta ~]# systemctl restart ipsec [root@tun-hosta ~]# ipsec auto --add tunnelVPN 002 "tunnelVPN": added IKEv2 connection
Fichier de conf Ipsec sur hostb
[root@tun-hosta ~]# scp /etc/ipsec.d/host_to_host.conf root@tun-hostb:/etc/ipsec.d/host_to_host.conf [root@tun-hostb ~]# ls -al /etc/ipsec.d/host_to_host.conf -rw-r--r--. 1 root root 1335 Jun 19 18:00 /etc/ipsec.d/host_to_host.conf
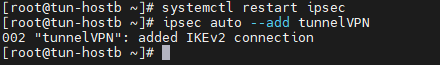
Mise en place du Tunnel Ipsec hostb – l’encapsulation tun0
[root@tun-hostb ~]# systemctl restart ipsec [root@tun-hostb ~]# ipsec auto --add tunnelVPN 002 "tunnelVPN": added IKEv2 connection
Monter le tunnelVPN sur les deux machines
[root@tun-hostb ~]# ipsec auto --up tunnelVPN
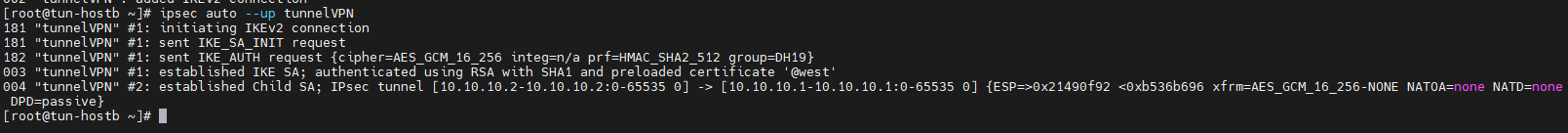
[root@tun-hosta ~]# ipsec auto --up tunnelVPN
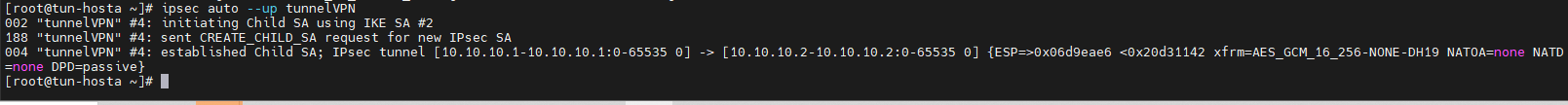
Check le tunnelVPN sur les deux machines
[root@tun-hosta ~]# ipsec verify
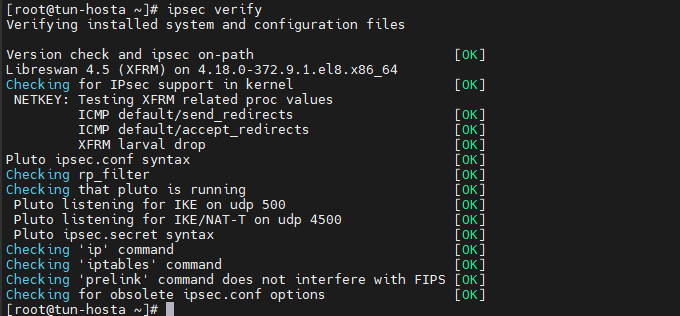
[root@tun-hostb ~]# ipsec verify

[root@tun-hosta ~]# journalctl -e

[root@tun-hostb ~]# journalctl -e

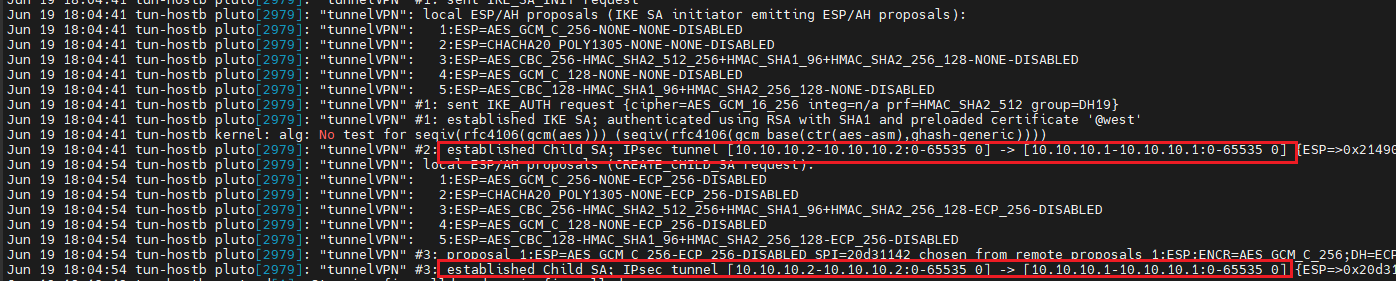
[root@tun-hosta ~]# ipsec show 10.10.10.1/32 <=> 10.10.10.2/32 using reqid 16389

[root@tun-hostb ~]# ipsec show 10.10.10.2/32 <=> 10.10.10.1/32 using reqid 16389

Ajouter des logs pour Ipsec (les deux machines)
[root@tun-hostx ~]# vi /etc/ipsec.conf logfile=/var/log/pluto.log [root@tun-hostx ~]# systemctl restart ipsec
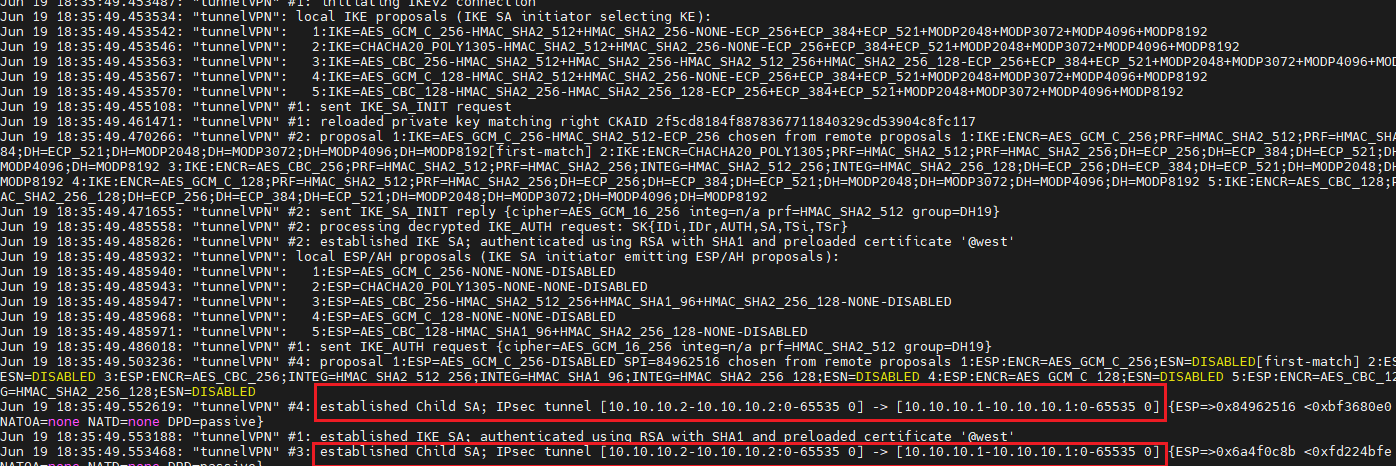
[root@tun-hosta ~]# tail -30 /var/log/pluto.log
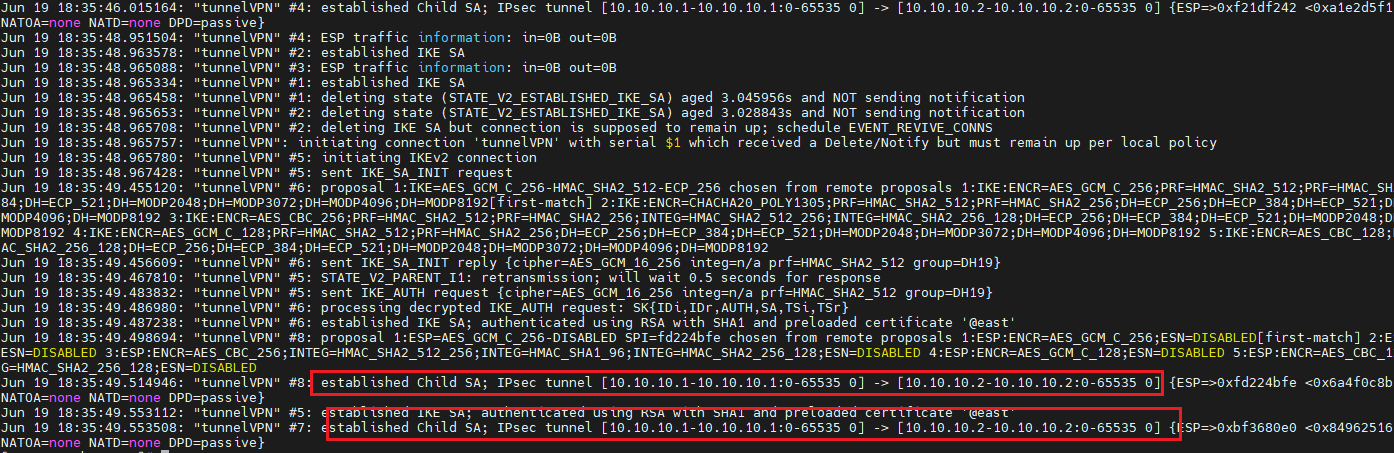
[root@tun-hostb ~]# tail -30 /var/log/pluto.log
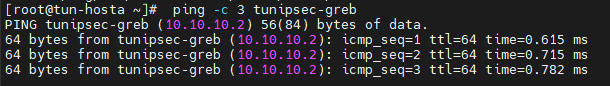
Check flux réseau
[root@tun-hosta ~]# ping -c 3 tunipsec-grea

[root@tun-hosta ~]# ping -c 3 tunipsec-greb
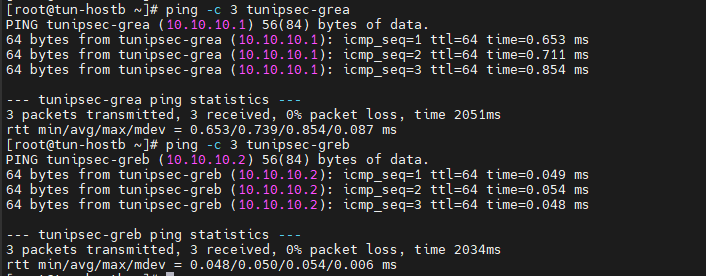
[root@tun-hostb ~]# ping -c 3 tunipsec-grea [root@tun-hostb ~]# ping -c 3 tunipsec-greb
Views: 8