Spécification de la machine vpn-ipsec-left.house.cpb
Host : vpn-ipsec-left.house.cpb
- IP :192.168.1.56
- OS : RockyLinux
- vCPU : 2
- DD : 8Go
- Ram : 2Go
Spécification de la machine vpn-ipsec-right.house.cpb
Host : vpn-ipsec-right.house.cpb
- IP :172.32.185.31
- OS : RockyLinux
- vCPU : 2
- DD : 8Go
- Ram : 2Go
Machine vpn-ipsec-left.house.cpb – Site A
Host : vpn-ipsec-left.house.cpb
- vSwitch : vmbr0
- IP :192.168.1.56
- OS : RockyLinux 8.4
- vCPU : 2
- DD : 8Go
- Ram : 2Go
Update de la machine
[root@vpn-ipsec-left ~]# dnf -y update
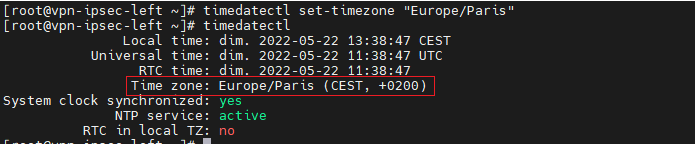
TimeDate
[root@vpn-ipsec-left ~]# timedatectl set-timezone "Europe/Paris" [root@vpn-ipsec-left ~]# timedatectl
Ajout des hosts machines (si pas de DNS)
[root@vpn-ipsec-left ~]# echo "192.168.1.56 vpn-ipsec-left vpn-ipsec-left.house.cpb" >> /etc/hosts [root@vpn-ipsec-left ~]# echo "172.32.185.31 vpn-ipsec-right vpn-ipsec-right.house.cpb" >> /etc/hosts
Désactiver « rp_filter » de Libreswan
[root@vpn-ipsec-left ~]# echo "net.ipv4.conf.all.rp_filter = 0" >> /etc/sysctl.d/50-libreswan.conf [root@vpn-ipsec-left ~]# sysctl --system
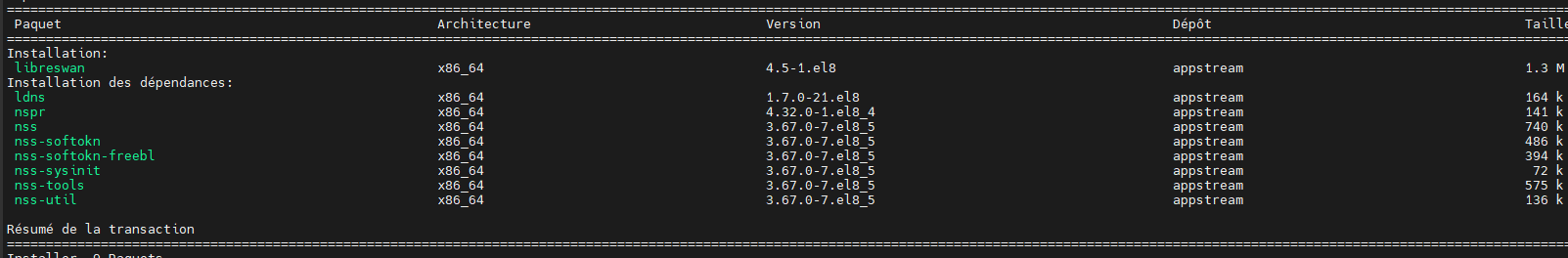
Installation package
[root@vpn-ipsec-left ~]# yum install libreswan

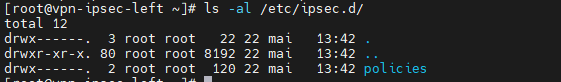
Initialiser la base nss
[root@vpn-ipsec-left ~]# systemctl stop ipsec [root@vpn-ipsec-left ~]# rm -f /etc/ipsec.d/*db [root@vpn-ipsec-left ~]# ls -al /etc/ipsec.d/
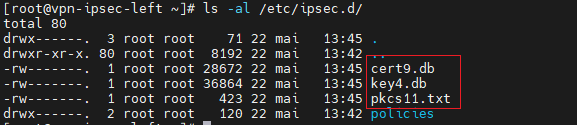
[root@vpn-ipsec-left ~]# ipsec initnss Initializing NSS database [root@vpn-ipsec-left ~]# ls -al /etc/ipsec.d/
Ajouter les règles Firewall
[root@vpn-ipsec-left ~]# firewall-cmd --add-service=ipsec --permanent [root@vpn-ipsec-left ~]# firewall-cmd --remove-service={cockpit,dhcpv6-client} --permanent [root@vpn-ipsec-left ~]# firewall-cmd --reload
Démarrer le service
[root@vpn-ipsec-left ~]# systemctl enable ipsec --now [root@vpn-ipsec-left ~]# systemctl status ipsec
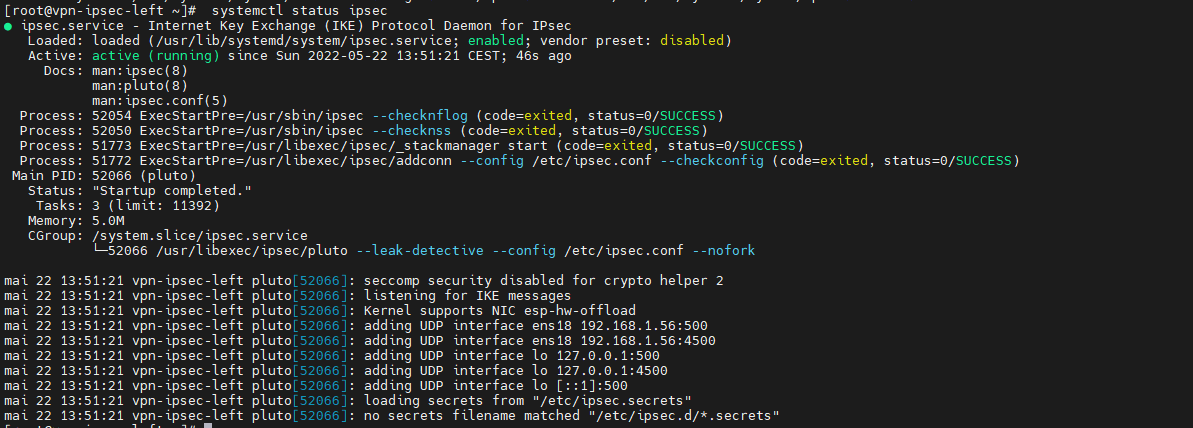
Générer une cléf RSA
[root@vpn-ipsec-left ~]# ipsec newhostkey Generated RSA key pair with CKAID f2f80cb679336256ac8c159b119464430d5bc7f9 was stored in the NSS database The public key can be displayed using: ipsec showhostkey --left --ckaid f2f80cb679336256ac8c159b119464430d5bc7f9 [root@vpn-ipsec-left ~]# ipsec showhostkey --left --ckaid f2f80cb679336256ac8c159b119464430d5bc7f9 # rsakey AwEAAb9Rf leftrsasigkey=0sAwEAAb9RfAkykozOv4VudJodKC0RmQ+w2TueEo8Ma7Pa/Ru73h+1xFMI77nSHhDxVbIrTwDtiimwz86wDPHtY7Uz7NOkQshjCflb2tp2nQzVi0tA8+qxjnPuLe0AUKRf03QwwY8TCv4kHcP7nd0rZs8MFPvHPao7fZj5u0UBfREWS5QfXbXgtDjaicC40t6QW5ngwm7AmaoXpyLPbBBU4VeVCRNSnjky6orRpMhkDOTAg0198Iz35jNRxf5J2BxBdRjGag5HpzAkbAJX9MjBMerBTzLAC+a1XvQzelJGTTLsbeqG2ziPW4HvZ6A33hMb6TRCbJPmTyuO2fb9i9YQlOQJgJP5GcA5AQYCu0nCYOuyrQcoBQPOOoDZ2e3thpGP37qkQMYffeRsXMgIVezHhI45pAM1wylWaaeo5f3HoYgiMHUJl6S1LD+xzDXmR1fQWF9t3++mJEEWClZuAyK67YboM6+PwUCidOS4p01ISxS1LdkGDF99l8b2H0S+urn/L2U+DjMYOBA/THkjwuM=
Création fichier Machine left ⬄ Machine right
[root@vpn-ipsec-left ~]# vi /etc/ipsec.d/host_to_host.conf
conn tunnelVPN
leftid=@west
left=192.168.1.56
Leftrsasigkey=0sAwEAAb9RfAkykozOv4VudJodKC0RmQ+w2TueEo8Ma7Pa/Ru73h+1xFMI77nSHhDxVbIrTwDtiimwz86wDPHtY7Uz7NOkQshjCflb2tp2nQzVi0tA8+qxjnPuLe0AUKRf03QwwY8TCv4kHcP7nd0rZs8MFPvHPao7fZj5u0UBfREWS5QfXbXgtDjaicC40t6QW5ngwm7AmaoXpyLPbBBU4VeVCRNSnjky6orRpMhkDOTAg0198Iz35jNRxf5J2BxBdRjGag5HpzAkbAJX9MjBMerBTzLAC+a1XvQzelJGTTLsbeqG2ziPW4HvZ6A33hMb6TRCbJPmTyuO2fb9i9YQlOQJgJP5GcA5AQYCu0nCYOuyrQcoBQPOOoDZ2e3thpGP37qkQMYffeRsXMgIVezHhI45pAM1wylWaaeo5f3HoYgiMHUJl6S1LD+xzDXmR1fQWF9t3++mJEEWClZuAyK67YboM6+PwUCidOS4p01ISxS1LdkGDF99l8b2H0S+urn/L2U+DjMYOBA/THkjwuM=
rightid=@east
right=172.32.185.31
rightrsasigkey=0sAwEAAdptcCuPX9bb9VoI+Y8jW8CJTXNPFqXrg5Q1AGqLfrr/2Pyc9m3GkkaBtZDIWVYAE5JpSHwFAwrAvONaeldppssCjsch8tRXTYOCD0MnI44VTn1L1b6L/ofECV/Hm1CIfzE82MJiIWekrfxfj34AnZplSPc8oTZZm7J0n4yEUC452Y7zeWBH/OA4vIFRnk8MY3JrsKMI3zt4LkFL828mWyXhqU2qLtNm/cjPf2wlczv0U6EgFIB8V6XmnD+TZZkBid0NziNrXKc/BdSRB4ZFk0VbH2BoM7TcwgQurAacODb6dWRxG+fxyYAn0STQbwfVUwcymVtAjQFj3jT0GAUbc6IdEQiQNuGuS6K0uhYWShODE+P9fSDWHZnIEtHGQzyU/BDUZnjwYAVV2h6kZvdFQoMOCGQYVM8PIWR8yZTR8hHdj2dsLb/XM/AzLJaf35bBSYAnp1RJRwjtMMjXraxJ2ijx/ssezw80gu3Bvj/ntyQDhzFMwQaa37mlqbsHdjxIy7504ylBOyILVkHdqSKZB83kT2XuFWkXHjHVD0yzu/rlE/zQmOaiKuGDgXp6DYUwQN7MM1XdT35DHSBlxrcVs91xusxgeYSD7zFI/WwZtPPf3Bm7BcAlQUz93brQLTr3WuRREDe/pqdT4xDrQw==
authby=rsasig
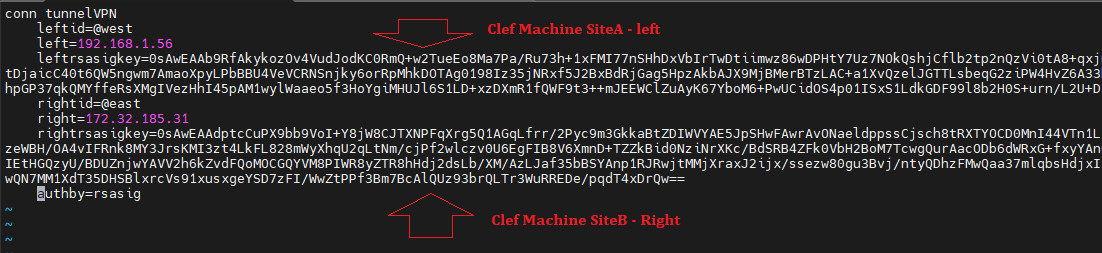
- En bleu : Clef site public A (left)
- En orange : Clef site public B (right)
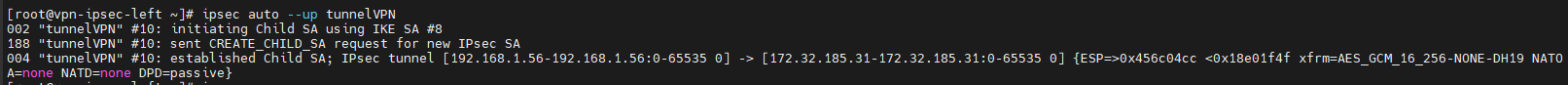
Mise en place du Tunnel
[root@vpn-ipsec-left ~]# systemctl restart ipsec [root@vpn-ipsec-left ~]# ipsec auto --add tunnelVPN 002 "tunnelVPN": added IKEv2 connection
LANCER La commande add tunelVPN sur les deux machines avant de lancer le UP
Quand le add tunnelVPN est lancé sur les deux machines.
[root@vpn-ipsec-left ~]# ipsec auto --up tunnelVPN
[root@vpn-ipsec-left ~]# ipsec verify

Machine vpn-ipsec-right.house.cpb – Site B
Host : vpn-ipsec-right.house.cpb
- vSwitch : vmbr2
- IP :172.32.185.31
- OS : RockyLinux 8.4
- vCPU : 2
- DD : 8Go
- Ram : 2Go
Update de la machine
[root@vpn-ipsec-right ~]# dnf -y update
TimeDate
[root@vpn-ipsec-right ~]# timedatectl set-timezone "Europe/Paris"
Ajout des hosts machine (si pas de DNS)
[root@vpn-ipsec-right ~]# echo "192.168.1.56 vpn-ipsec-left vpn-ipsec-left.house.cpb" >> /etc/hosts [root@vpn-ipsec-right ~]# echo "172.32.185.31 vpn-ipsec-right vpn-ipsec-right.house.cpb" >> /etc/hosts
Installation package
[root@vpn-ipsec-right ~]# yum install libreswan
Initialiser la base nss
[root@vpn-ipsec-right ~]# systemctl stop ipsec [root@vpn-ipsec-right ~]# rm -f /etc/ipsec.d/*db [root@vpn-ipsec-right ~]# ls -al /etc/ipsec.d/ [root@vpn-ipsec-right ~]# ipsec initnss Initializing NSS database
Ajouter les règles Firewall
[root@vpn-ipsec-right ~]# firewall-cmd --add-service=ipsec --permanent [root@vpn-ipsec-right ~]# firewall-cmd --remove-service={cockpit,dhcpv6-client} --permanent [root@vpn-ipsec-right ~]# firewall-cmd --reload
Désactiver « rp_filter » de Libreswan
[root@vpn-ipsec-right ~]# echo "net.ipv4.conf.all.rp_filter = 0" >> /etc/sysctl.d/50-libreswan.conf [root@vpn-ipsec-right ~]# sysctl --system
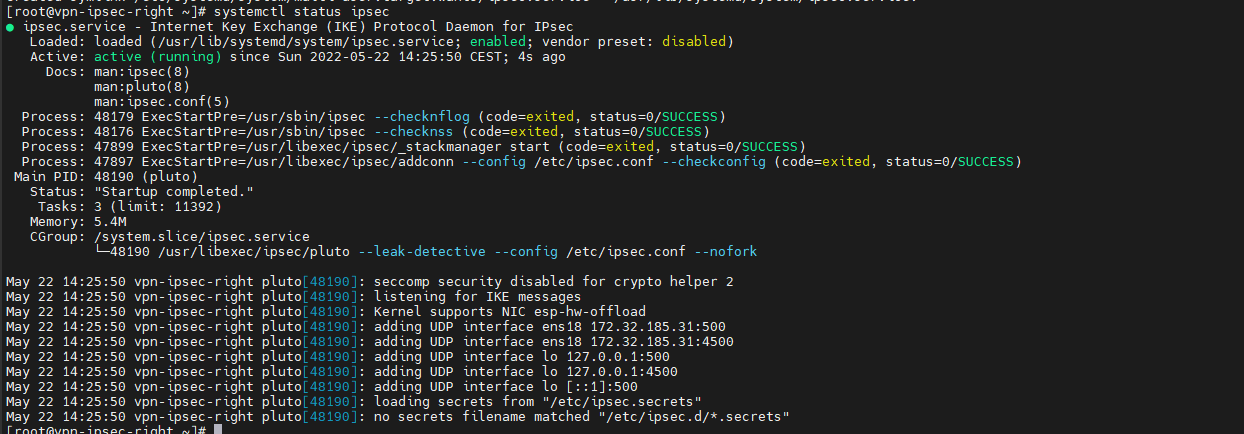
Démarrer le service
[root@vpn-ipsec-right ~]# systemctl enable ipsec --now [root@vpn-ipsec-right ~]# systemctl status ipsec
Générer une cléf RSA
[root@vpn-ipsec-right ~]# ipsec newhostkey Generated RSA key pair with CKAID 957f4e4b42de1ec6a61af4e58796747e5dc264b3 was stored in the NSS database The public key can be displayed using: ipsec showhostkey --left --ckaid 957f4e4b42de1ec6a61af4e58796747e5dc264b3 [root@vpn-ipsec-right ~]# ipsec showhostkey --right --ckaid 957f4e4b42de1ec6a61af4e58796747e5dc264b3 # rsakey AwEAAdptc rightrsasigkey=0sAwEAAdptcCuPX9bb9VoI+Y8jW8CJTXNPFqXrg5Q1AGqLfrr/2Pyc9m3GkkaBtZDIWVYAE5JpSHwFAwrAvONaeldppssCjsch8tRXTYOCD0MnI44VTn1L1b6L/ofECV/Hm1CIfzE82MJiIWekrfxfj34AnZplSPc8oTZZm7J0n4yEUC452Y7zeWBH/OA4vIFRnk8MY3JrsKMI3zt4LkFL828mWyXhqU2qLtNm/cjPf2wlczv0U6EgFIB8V6XmnD+TZZkBid0NziNrXKc/BdSRB4ZFk0VbH2BoM7TcwgQurAacODb6dWRxG+fxyYAn0STQbwfVUwcymVtAjQFj3jT0GAUbc6IdEQiQNuGuS6K0uhYWShODE+P9fSDWHZnIEtHGQzyU/BDUZnjwYAVV2h6kZvdFQoMOCGQYVM8PIWR8yZTR8hHdj2dsLb/XM/AzLJaf35bBSYAnp1RJRwjtMMjXraxJ2ijx/ssezw80gu3Bvj/ntyQDhzFMwQaa37mlqbsHdjxIy7504ylBOyILVkHdqSKZB83kT2XuFWkXHjHVD0yzu/rlE/zQmOaiKuGDgXp6DYUwQN7MM1XdT35DHSBlxrcVs91xusxgeYSD7zFI/WwZtPPf3Bm7BcAlQUz93brQLTr3WuRREDe/pqdT4xDrQw==
Récupération de la Conf Client left (certificats left et right)
[root@vpn-ipsec-left ~]# scp /etc/ipsec.d/host_to_host.conf root@vpn-ipsec-right:/etc/ipsec.d/host_to_host.conf [root@vpn-ipsec-right ~]# ls -al /etc/ipsec.d/host_to_host.conf -rw-r--r--. 1 root root 1353 May 22 14:50 /etc/ipsec.d/host_to_host.conf
Mise en place Tunnel entre les Hosts
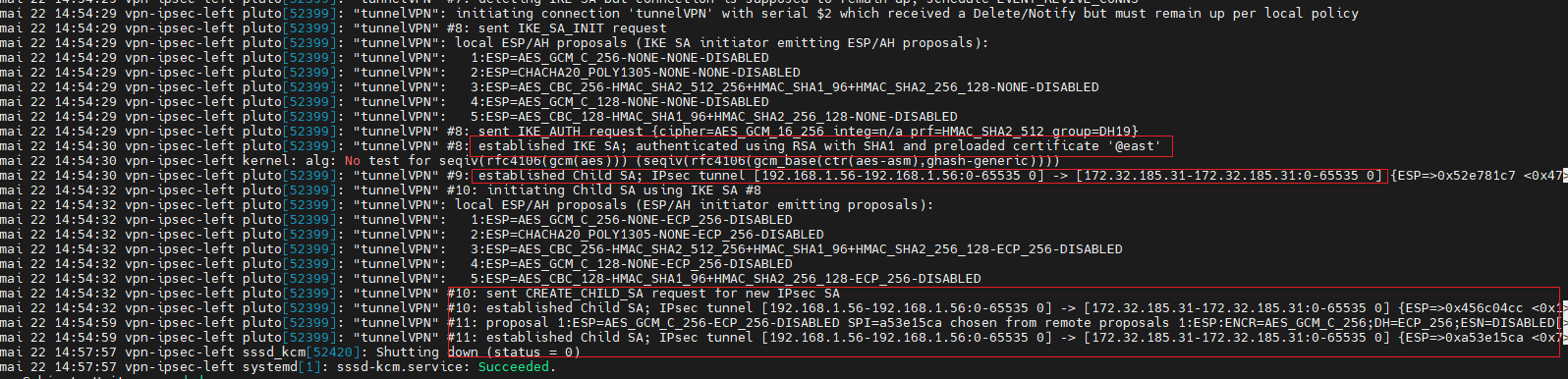
[root@vpn-ipsec-right ~]# systemctl restart ipsec [root@vpn-ipsec-right ~]# ipsec auto --add tunnelVPN 002 "tunnelVPN": added IKEv2 connection [root@vpn-ipsec-right ~]# ipsec auto --up tunnelVPN

[root@vpn-ipsec-right ~]# ipsec verify
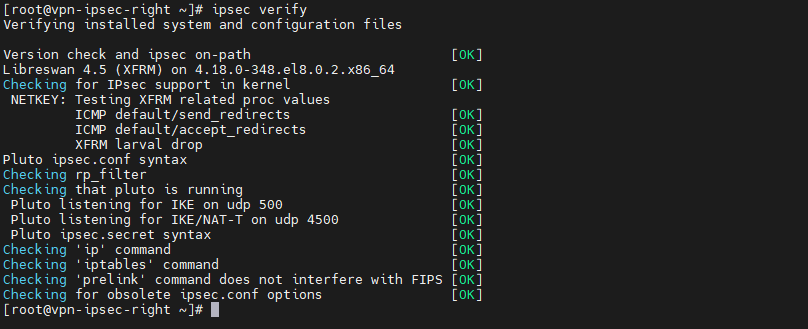
Check le Tunnel entre les Hosts (2 machines)
Sur vpn-ipsec-right
[root@vpn-ipsec-right ~]# journalctl –xe

Sur vpn-ipsec-left
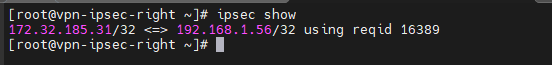
[root@vpn-ipsec-left ~]# ipsec show 192.168.1.56/32 <=> 172.32.185.31/32 using reqid 16389

[root@vpn-ipsec-right ~]# ipsec show 172.32.185.31/32 <=> 192.168.1.56/32 using reqid 16389
[root@vpn-ipsec-left ~]# ipsec look
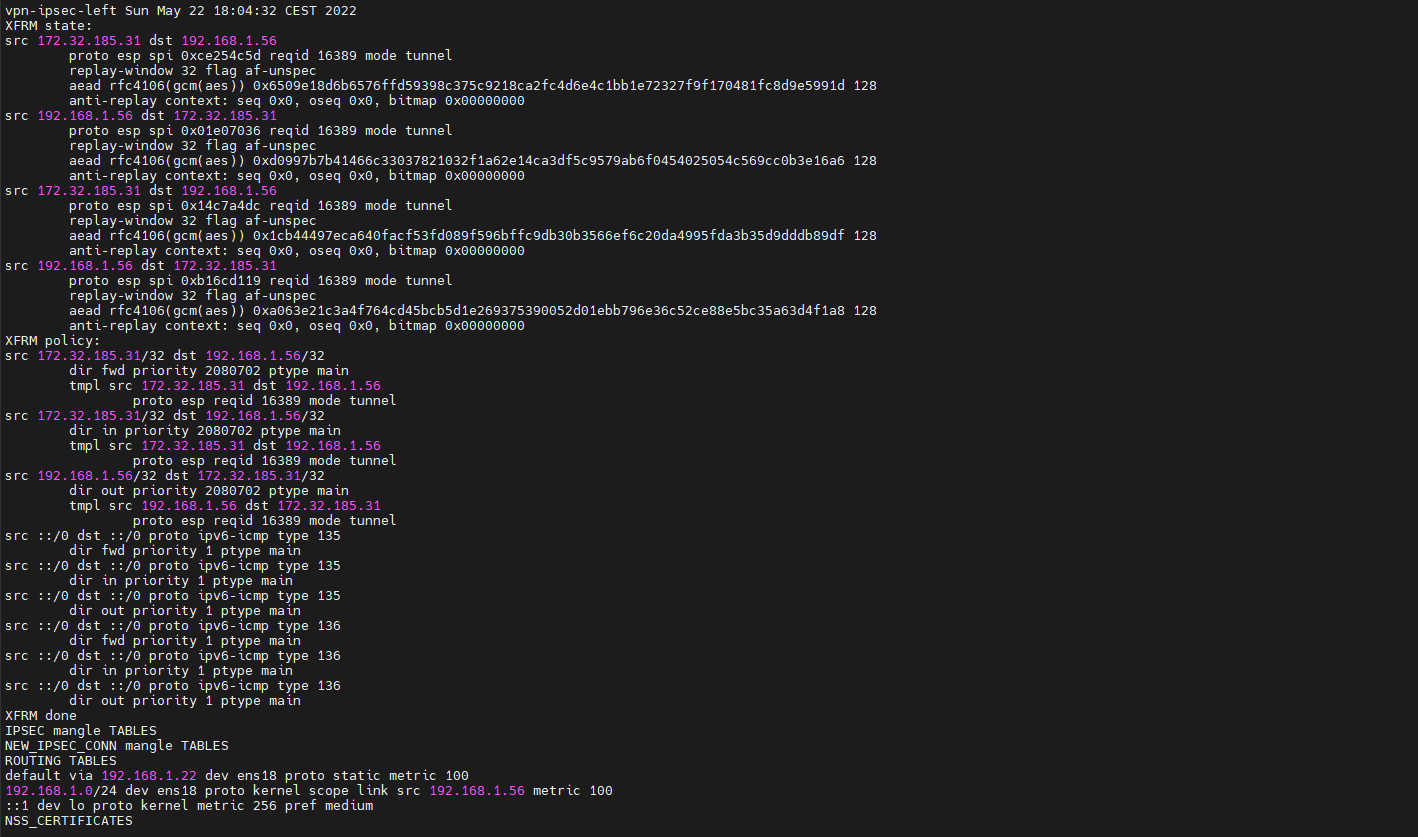
Le tunnel VPN est bien étable entre les deux clients 192.168.1.56 vers 172.32.185.31
Ajoutons les logs(2 machines)
Editer le fichier /etc/ipsec.conf
[root@vpn-ipsec-xxx~]# vi /etc/ipsec.conf
config setup
# If logfile= is unset, syslog is used to send log messages too.
# Note that on busy VPN servers, the amount of logging can trigger
# syslogd (or journald) to rate limit messages.
logfile=/var/log/pluto.log
Restart ipsec – vpn-ipsec-left
[root@vpn-ipsec-left ~]# systemctl restart ipsec [root@vpn-ipsec-left ~]# ipsec auto --add tunnelVPN
Restart ipsec – vpn-ipsec-right
[root@vpn-ipsec-right ~]# systemctl restart ipsec [root@vpn-ipsec-right ~]# ipsec auto --add tunnelVPN
Restart tunnelVPN – vpn-ipsec-left et vpn-ipsec-right
[root@vpn-ipsec-left ~]# ipsec auto --up tunnelVPN [root@vpn-ipsec-right ~]# ipsec auto --up tunnelVP
Check le log pluto
Check – vpn-ipsec-left
[root@vpn-ipsec-left ~]# tail -30 /var/log/pluto.log
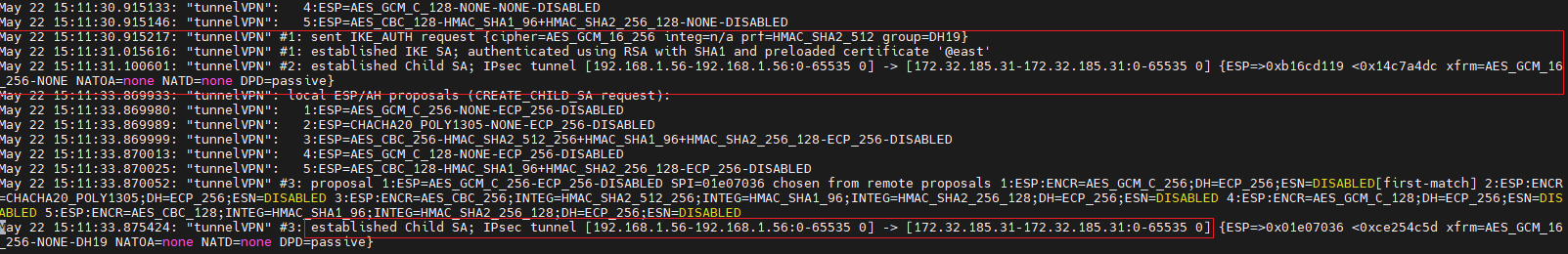
Check – vpn-ipsec-right
[oot@vpn-ipsec-right ~]# tail -30 /var/log/pluto.log

Ajoutons VPN start Automatique (2 machines)
[root@vpn-ipsec-right ~]# echo " auto=start" >> /etc/ipsec.d/host_to_host.conf [root@vpn-ipsec-left ~]# echo " auto=start" >> /etc/ipsec.d/host_to_host.conf [root@vpn-ipsec-left ~]# cat /etc/ipsec.d/host_to_host.conf

[root@vpn-ipsec-left ~]# ipsec stop && ipsec start [root@vpn-ipsec-left ~]# ipsec status
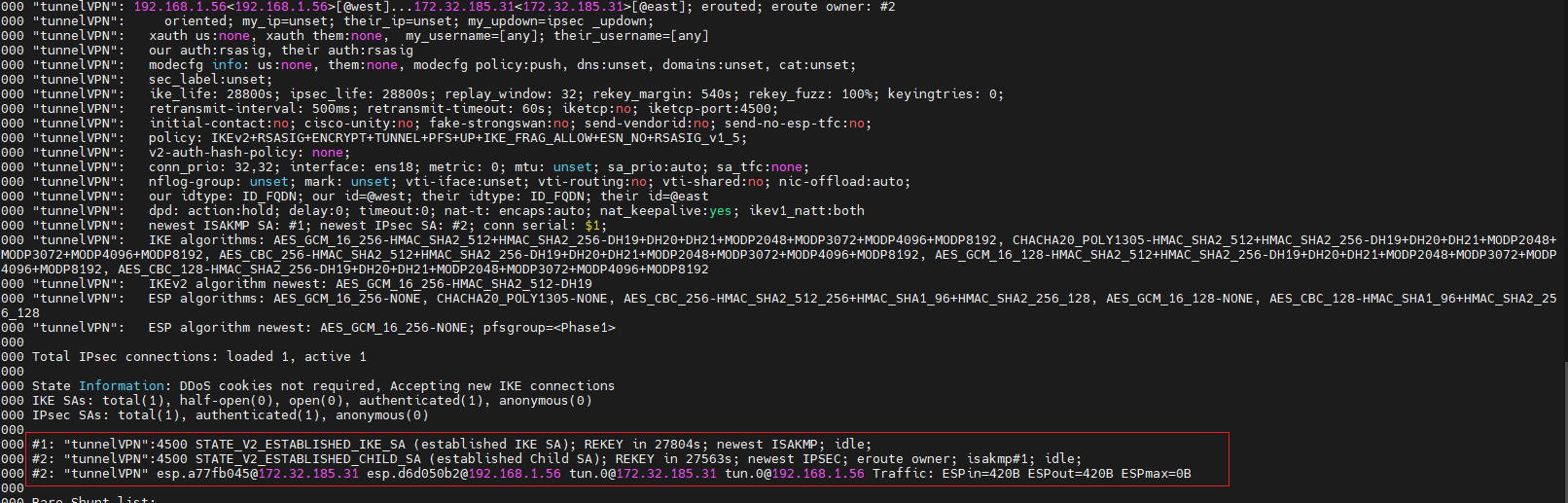
[root@vpn-ipsec-right ~]# ipsec stop && ipsec start [root@vpn-ipsec-right ~]# ipsec status

[root@vpn-ipsec-left ~]# ping -c 3 vpn-ipsec-right
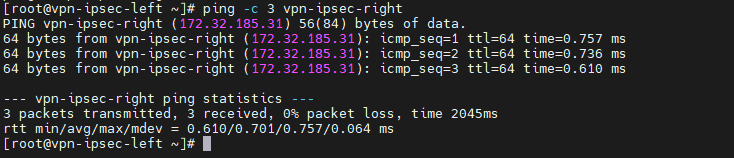
[root@vpn-ipsec-right ~]# ping -c 3 vpn-ipsec-left
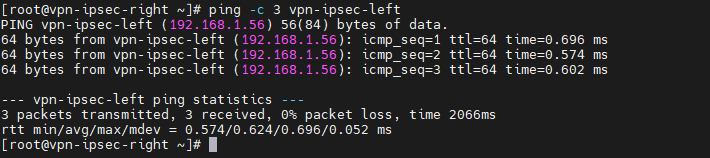
[root@vpn-ipsec-right ~]# ipsec showstates

Check Transaction SSL entre vpn-ipsec-right => vpn-ipsec-left
Installation tcpflow sur vpn-ipsec-left
[root@vpn-ipsec-left ~]#dnf install wget [root@vpn-ipsec-left ~]#dnf install https://forensics.cert.org/cert-forensics-tools-release-el8.rpm [root@vpn-ipsec-left ~]#dnf install epel-release [root@vpn-ipsec-left ~]#dnf --enablerepo=forensics install tcpflow
Lancement une écoute sur port 22 sur vpn-ipsec-left
[root@vpn-ipsec-left ~]# tcpflow -c -p -i any dst port 22 >> ecoute.txt |tail -f ecoute.txt
Lancement d’un copie de fichier – vpn-ipsec-right => vpn-ipsec-left
[root@vpn-ipsec-right chris]# touch titi.txt [root@vpn-ipsec-right chris]# scp titi.txt root@192.168.1.56:/home/chris/toto.txt [root@vpn-ipsec-left ~]# cat ecoute.txt

Views: 3